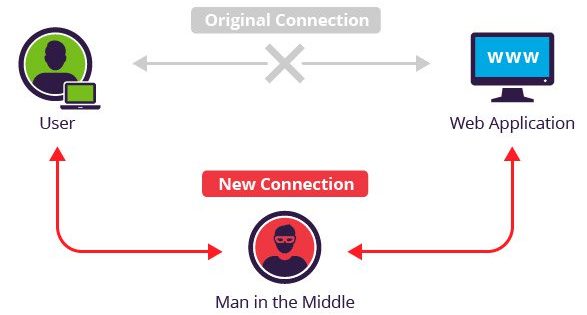
Ledger hardware wallets, once considered one of the safer methods to store cryptocurrency, have been reported to be vulnerable to “man in the middle” attacks.
The Flaw
A team of unknown security researchers exposed a vulnerability that allegedly involves all Ledger hardware wallets. The discovery of the issue is said to have affected over one million users and has made it evident that the devices are not a foolproof method of storing crypto.
The newfound threat allows cybercriminals to show fraudulent addresses to ledger users/ customers in order to drain the user’s wallet and transfer the contents into their own wallet.
The problem was addressed by Ledger on February 3rd when the company Tweeted a report containing details of the vulnerability. The report offers preventative steps to avoid falling victim to attack but does not offer a real fix or solution.
To mitigate the man in the middle attack vector reported here https://t.co/GFFVUOmlkk (affecting all hardware wallet vendors), always verify your receive address on the device's screen by clicking on the "monitor button" pic.twitter.com/EMjZJu2NDh
— Ledger (@LedgerHQ) February 3, 2018
The security researchers behind the discovery reported that Ledger did not take the findings seriously, saying
We contacted the CEO and CTO of Ledger directly in order to privately disclose and fix the issue. We’ve received a single reply, asking to hand over the attack details. Since then, all our mail have been ignored for three weeks, finally receiving an answer that they won’t issue any fix/ change.
Instead, the company plans on raising public awareness so that users can protect themselves from these types of attacks.
How It’s Done
A Ledger wallet creates a brand new address every time a payment is to be received, however, a man-in-the-middle attack will transfer the cryptocurrency to a fraudulent address instead of the user’s wallet. The report released by Ledger states that the attack is carried out when a Ledger customer uses a computer infected with malware, allowing the cybercriminal to interfere with the addresses that the cryptocurrency is intended for.
Once the computer is compromised, the attacker can discreetly change the code used to generate the unique address and, consequently, deposit the balance in their own wallet.
This is due to the wallet using a JavaScript code running on the computer. A computer infected with the malware only needs to replace the code that generates the receiving address with a code that leads to the attacker’s wallet.
Preventing Attack
The report went on to mention suggestions for preventing an attack. It stresses that users verify the wallet address that funds are being sent to before transferring. A user can check this by clicking on the button below the QR Code to display the address of the hardware wallet and verify it. (Shown above in Tweet)
As it continues, the report explains that the module is not applicable on the Ether wallet interface from Ledger due to the fact that the Ethereum app does not have mitigation, leaving the user unable to confirm whether the address is correct or not. As a result, the unnamed authors of the report suggested
If you’re using the Ethereum App – Treat the Ledger hardware wallet the same as any other software-based wallet, and use it only on a Live CD operating system that is guaranteed to be malware-free. At least until this issue receives some kind of fix.
Do you have a Ledger product? What are your thoughts on these new attacks? Let us know in the comments below!
Images courtesy of Pixabay, LinkedIn
The post Ledger Hardware Wallets Vulnerable to ‘Man in the Middle’ Attacks appeared first on Bitcoinist.com.